A Site to Site VPN can be setup between your home and business, two office locations, or between family members. Some common use cases would be to share files, printers, provide technical support (RDP/VNC), view webcams (without opening webcam to the internet) and my favorite, as a mean for secure offsite backups.
By going through this tutorial you'll also learn:
- How to setup a Certificate Authority on your router and generate Certificates and Keys
- Setup (free) Dynamic DNS
- Setup cross site name resolution (static DNS host entries)
- A little bit on expanding the setup to include Client to Site VPN
- How to enable SFTP on your router for secure access to certificates and keys
Last updated and verified on 3/3/2014
Here's a video walk-through of the whole process (24 minutes!). Note that this video is a little dated and should only be used as a reference. This blog has the correct instructions:
What you'll need:
- Two routers with Tomato already installed.*
- The OpenVPN Server router should be running TomatoUSB (with a USB port)
- The OpenVPN Client router can run regular Tomato (no USB port required)
- USB Flash Drive >=1GB (will be completely wiped)
- Publicly accessible IP address for OpenVPN Server router.
Outline of Steps
1) Setup OpenVPN Server on Site A Router
b) Generate RSA Certificates and Keys
c) Configure OpenVPN Server
d) Setup Free Dynamic DNS Service
e) Start OpenVPN Server
a) Configure OpenVPN Client
4) That's it! Enjoy.
Network Info
Site A
OpenVPN Server
Internal network/subnetmask - 192.168.1.0/255.255.255.0
External Public IP Address
Site B
OpenVPN Client
Internal network/subnetmask - 192.168.2.0/255.255.255.0
External Public IP Address
-------------------------------------------------------------------------------
LETS GET STARTED!
Setup OpenVPN Server on Site A Router
Plug in USB flash drive. Make sure the router has internet access.
Connect via SSH into router. For Windows, I recommend Putty.
Log in with username of root and password of admin.
Execute the following commands:
#Partition your usb flash drive
umount /dev/sda1
fdisk /dev/sda
#format newly created partition
#label disk as 'optware' case sensitive
umount /dev/sda1
mke2fs -j -L optware /dev/sda1
Install Entware (a package manager that allows you to install additional software on your router)
Setup Certificate Authority (CA)
#Setup and initialize environment
cd /opt/etc/easy-rsa
ca /opt/etc/easy-rsa/keys/ca.crt
On your router, go to Basic -> DDNS (http://192.168.1.1/basic-ddns.asp)
For Dynamic DNS 1, select "FreeDNS(afraid.org)" in the "Service" dropdown.
Paste in the URL you copied in the previous step (note that the URL will change to a token)
Check "Force next update"
Change the "Auto refresh every" to 7 or something lower than 30.
[Save]
Last Result should say Update Successfully.
Start OpenVPN Server
Go to VPN Tunneling -> OpenVPN Server (http://192.168.1.1/vpn-server.asp).
On "Server 1 -> Status" Tab, click the "Start Now" button. Give it a few seconds and click on the "Refresh Status" link.
If you see the following, then the OpenVPN Server has started successfully. Congratulations we're almost there. Note that the button will change to "Stop Now". If the button remains as "Start Now", we have a problem. Go back and review the instructions.
Cross Site Name Resolution
At this point your Site to Site VPN is setup, but you'll only able to access network resources via IP Addresses.
To access network resources via a friendly name, you'll need to do two things:
1) Setup static DHCP lease reservation for the network device (you don't want the IP address changing)
- Go to Basic->Static DHCP/ARP/IPT
2) On the opposite router, setup a static WINS/DNS entry for the same network device
Go to Basic->Static DHCP/ARP/IPT. Typically the Static DHCP/ARP/IPT screen is for configuring static DHCP lease reservation, however you can use for static WINS/DNS entries also. The secret is to leave the MAC Address blank or with all zeros, "00:00:00:00:00".
In the screenshot below, on SiteB, I've setup a static hostname of "SiteARouter" so that I can access it via the friendly name versus the IP Address (192.168.1.1). From SiteB, I'm now able to access SiteARouter via name. Configure static hostname entries for all network resources you want to access on both your VPN sites.
That's it!! Enjoy.
Client to Site VPN
You should easily be able to add additional OpenVPN Clients (for Client to Site VPN) by generating additional RSA Certs/Key on your OpenVPN Server Router.
4) That's it! Enjoy.
Network Info
Site A
OpenVPN Server
Internal network/subnetmask - 192.168.1.0/255.255.255.0
External Public IP Address
Site B
OpenVPN Client
Internal network/subnetmask - 192.168.2.0/255.255.255.0
External Public IP Address
LETS GET STARTED!
Setup OpenVPN Server on Site A Router
Plug in USB flash drive. Make sure the router has internet access.
Connect via SSH into router. For Windows, I recommend Putty.
Log in with username of root and password of admin.
Execute the following commands:
#Partition your usb flash drive
umount /dev/sda1
fdisk /dev/sda
Type in the following commands to create a primary partition on your USB Flash drive
# p # list current partitions
# o # to delete all partitions
# n # new partition
# p # primary partition
# 1 (one) # first partition
# <enter> # default start block
# <enter> # default end block #use the whole flash drive
# w # write new partition to disk
# p # list current partitions
# o # to delete all partitions
# n # new partition
# p # primary partition
# 1 (one) # first partition
# <enter> # default start block
# <enter> # default end block #use the whole flash drive
# w # write new partition to disk
#format newly created partition
#label disk as 'optware' case sensitive
umount /dev/sda1
mke2fs -j -L optware /dev/sda1
Install Entware (a package manager that allows you to install additional software on your router)
#mount the new disk partition
mount /dev/sda1 /opt
cd /opt
wget http://wl500g-repo.googlecode.com/svn/ipkg/entware_install.sh
sh ./entware_install.sh
Install openvpn-easy-rsa
opkg install openvpn-easy-rsa nano
Setup working folder for openvpn-easy-rsa
It's recommended that you cut/paste everything up to Setup CA section into your console window to prevent any error/typos
#copy files to working directory
cd /opt/etc/easy-rsa
cp /opt/sbin/sign-req .
cp /opt/sbin/build-req .
cp /opt/sbin/inherit-inter .
cp /opt/sbin/revoke-full .
cp /opt/sbin/clean-all .
cp /opt/sbin/build-ca .
cp /opt/sbin/pkitool .
cp /opt/sbin/build-dh .
cp /opt/sbin/build-key-pass .
cp /opt/sbin/build-key-pkcs12 .
cp /opt/sbin/list-crl .
cp /opt/sbin/whichopensslcnf .
cp /opt/sbin/build-key-server .
cp /opt/sbin/build-key .
cp /opt/etc/easy-rsa/openssl-1.0.0.cnf .
cp /opt/sbin/build-inter .
cp /opt/sbin/build-req-pass .
#reduce key_size to 1024 in vars file
cd /opt/etc/easy-rsa
sed -i 's:KEY_SIZE=2048:KEY_SIZE=1024:' ./vars
#update PATH to pick up correct openssl (save a reboot)
#correct = /opt/bin/openssl
PATH=/opt/bin:$PATH
mount /dev/sda1 /opt
cd /opt
wget http://wl500g-repo.googlecode.com/svn/ipkg/entware_install.sh
sh ./entware_install.sh
#Make sure /opt is properly mounted on a reboot.
echo "LABEL=optware /opt ext3 defaults 1 1" >> /etc/fstab
nvram setfile2nvram /etc/fstab
nvram commit
Install openvpn-easy-rsa
opkg install openvpn-easy-rsa nano
Setup working folder for openvpn-easy-rsa
It's recommended that you cut/paste everything up to Setup CA section into your console window to prevent any error/typos
#copy files to working directory
cd /opt/etc/easy-rsa
cp /opt/sbin/sign-req .
cp /opt/sbin/build-req .
cp /opt/sbin/inherit-inter .
cp /opt/sbin/revoke-full .
cp /opt/sbin/clean-all .
cp /opt/sbin/build-ca .
cp /opt/sbin/pkitool .
cp /opt/sbin/build-dh .
cp /opt/sbin/build-key-pass .
cp /opt/sbin/build-key-pkcs12 .
cp /opt/sbin/list-crl .
cp /opt/sbin/whichopensslcnf .
cp /opt/sbin/build-key-server .
cp /opt/sbin/build-key .
cp /opt/etc/easy-rsa/openssl-1.0.0.cnf .
cp /opt/sbin/build-inter .
cp /opt/sbin/build-req-pass .
#reduce key_size to 1024 in vars file
cd /opt/etc/easy-rsa
sed -i 's:KEY_SIZE=2048:KEY_SIZE=1024:' ./vars
#update PATH to pick up correct openssl (save a reboot)
#correct = /opt/bin/openssl
PATH=/opt/bin:$PATH
Setup Certificate Authority (CA)
#Setup and initialize environment
cd /opt/etc/easy-rsa
source ./vars
./clean-all
#Select Default for All, Keep Hitting <Enter> (8 times)
./build-ca
Generate Diffie Hellman parameters (DH file)
./build-dh
Generate Certificate and Key for the OpenVPN Server router at Site A with Common Name [CN] of "OpenVPNServer".
#Generate Cert/Key for Site2SiteClient
#<Enter> 10 times to take default value
#Followed by two 'y' <Enter> when asked to sign and commit
./build-key-server OpenVPNServer
Generate Certificate and Key for the OpenVPN Client router Site B with Common Name [CN] of "Site2SiteClient". The "Common Name" isn't really "common". Make sure its unique for all your clients.
#Generate Cert/Key for Site2SiteClient
#<Enter> 10 times to take default value
#Followed by two 'y' <Enter> when asked to sign and commit
./build-key Site2SiteClient
Output Certificate and Key to console - cut/paste into text file for later use.
cat /opt/etc/easy-rsa/keys/ca.crt
cat /opt/etc/easy-rsa/keys/Site2SiteClient.crt
cat /opt/etc/easy-rsa/keys/Site2SiteClient.key
Create a new text file on your computer and name it "ClientRouterKeys.txt" and cut and paste in the output of the three cat commands above. You'll need this file to setup the OpenVPN Client Router later in the tutorial.
That's it for the SSH Console. The rest of the configuration will be done via a web browser.
Configure OpenVPN Server
#Select Default for All, Keep Hitting <Enter> (8 times)
./build-ca
Generate Diffie Hellman parameters (DH file)
./build-dh
Generate Certificate and Key for the OpenVPN Server router at Site A with Common Name [CN] of "OpenVPNServer".
#Generate Cert/Key for Site2SiteClient
#<Enter> 10 times to take default value
#Followed by two 'y' <Enter> when asked to sign and commit
./build-key-server OpenVPNServer
Generate Certificate and Key for the OpenVPN Client router Site B with Common Name [CN] of "Site2SiteClient". The "Common Name" isn't really "common". Make sure its unique for all your clients.
#Generate Cert/Key for Site2SiteClient
#<Enter> 10 times to take default value
#Followed by two 'y' <Enter> when asked to sign and commit
./build-key Site2SiteClient
Output Certificate and Key to console - cut/paste into text file for later use.
cat /opt/etc/easy-rsa/keys/ca.crt
cat /opt/etc/easy-rsa/keys/Site2SiteClient.crt
cat /opt/etc/easy-rsa/keys/Site2SiteClient.key
Create a new text file on your computer and name it "ClientRouterKeys.txt" and cut and paste in the output of the three cat commands above. You'll need this file to setup the OpenVPN Client Router later in the tutorial.
That's it for the SSH Console. The rest of the configuration will be done via a web browser.
Configure OpenVPN Server
Open your favorite browser and connect to your router and go to VPN Tunneling -> OpenVPN Server (http://192.168.1.1/vpn-server.asp).
On "Server 1 -> Basic" Tab, check "Start with WAN". Leave everything else as default.
OpenVPN Server Configuration Server 1->Basic Screen should look like the following:
On "Server 1 -> Basic" Tab, check "Start with WAN". Leave everything else as default.
OpenVPN Server Configuration Server 1->Basic Screen should look like the following:
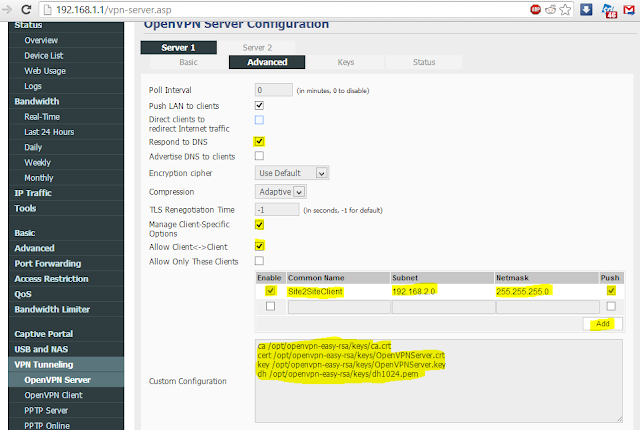
Change to the Advanced Tab
Check "Respond to DNS"
Check "Manage Client-Specific Options"
Check "Allow Client<->Client"
Check "Enable"
Type in "Site2SiteClient" under "Common Name"
Type in "192.168.2.0" under Subnet
Type in "255.255.255.0" under Netmask
Check Push
Click 'Add' button. (pushes routes to the client router and add route to server router. No need for router/iptable commands)
In the "Custom Configuration" box, paste in the following (saves us from pasting in the certs/key in the Keys Tab and valuable nvram space):
ca /opt/etc/easy-rsa/keys/ca.crt
cert /opt/etc/easy-rsa/keys/OpenVPNServer.crt
key /opt/etc/easy-rsa/keys/OpenVPNServer.key
key /opt/etc/easy-rsa/keys/OpenVPNServer.key
dh /opt/etc/easy-rsa/keys/dh1024.pem
[Save]
Setup Free Dynamic DNS Service (http://freedns.afraid.org/)
If you don't have a public static IP (most don't), you'll need to setup DDNS so your OpenVPN client(s) can find your OpenVPN server.
If you don't have a public static IP (most don't), you'll need to setup DDNS so your OpenVPN client(s) can find your OpenVPN server.
Go to http://freedns.afraid.org and setup an account and then setup a subdomain.
I'm using "OpenVPNServer.mooo.com" (use something else). We'll need this subdomain during the OpenVPN Client setup.
I'm using "OpenVPNServer.mooo.com" (use something else). We'll need this subdomain during the OpenVPN Client setup.
On the left hand side, select "Dynamic DNS" or go to http://freedns.afraid.org/dynamic
Find the subdomain you just created and right click on the "Direct URL" link and select "Copy link address"
On your router, go to Basic -> DDNS (http://192.168.1.1/basic-ddns.asp)
For Dynamic DNS 1, select "FreeDNS(afraid.org)" in the "Service" dropdown.
Paste in the URL you copied in the previous step (note that the URL will change to a token)
Check "Force next update"
Change the "Auto refresh every" to 7 or something lower than 30.
[Save]
Last Result should say Update Successfully.
Start OpenVPN Server
Go to VPN Tunneling -> OpenVPN Server (http://192.168.1.1/vpn-server.asp).
On "Server 1 -> Status" Tab, click the "Start Now" button. Give it a few seconds and click on the "Refresh Status" link.
If you see the following, then the OpenVPN Server has started successfully. Congratulations we're almost there. Note that the button will change to "Stop Now". If the button remains as "Start Now", we have a problem. Go back and review the instructions.
Configuration of Site A Router is complete. Go ahead and reboot the router and verify that OpenVPN Server started properly.
Let's move on to setting up your Site B Router.
Setup OpenVPN Client on Site B Router
Configure OpenVPN Client
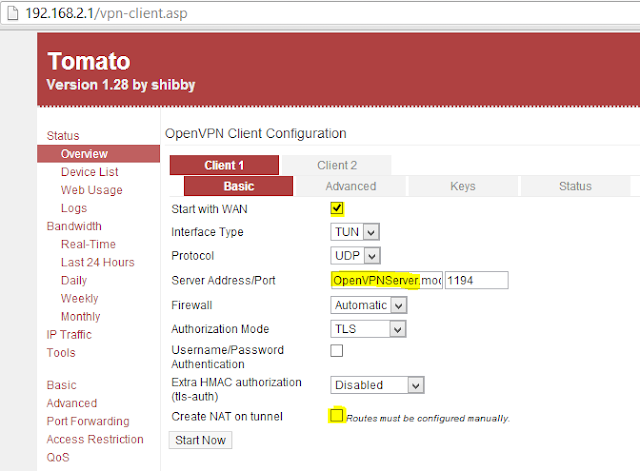
At Site B, open up your browser and go to VPN Tunneling -> OpenVPN Client (http://192.168.2.1/vpn-client.asp). Go to Client 1 -> Basic.
Type in the Dynamic DNS address (subdomain) you setup for your Site A router in the "Server Address" field. In my example, "OpenVPNServer.mooo.com"
Uncheck the "Connect NAT on tunnel"
Check "Start with WAN"
[Save]
Nothing has to be changed on the Client 1 -> Advanced Tab
Open up the Client 1 -> Keys Tab.
Open up "ClientRouterKeys.txt" file you created earlier in the tutorial and cut/paste the certificates and key into the appropriate field.
ca.crt in the Certificate Authority box
Site2SiteClient.crt in the Client Certificate box
Site2SiteClient.key in the Client Key box
Don't forget to [Save].
Your done with the configuration. The moment of truth, on the Client 1 -> Status Tab, Click "Start Now"
Wait a few seconds and click on the "Refresh Status" link. Hopefully you'll see some bytes in the Value column.
From Site B, you should now be able to access Site A network resources and vice-versa.
Lets give the VPN a quick test. Still connected to Site B, open up the OpenVPN Server Configuration page on your Site A router @ http://192.168.1.1/vpn-server.asp. Hopefully you can see a successfully status page like the one below:
Let's move on to setting up your Site B Router.
Setup OpenVPN Client on Site B Router
Configure OpenVPN Client
At Site B, open up your browser and go to VPN Tunneling -> OpenVPN Client (http://192.168.2.1/vpn-client.asp). Go to Client 1 -> Basic.
Type in the Dynamic DNS address (subdomain) you setup for your Site A router in the "Server Address" field. In my example, "OpenVPNServer.mooo.com"
Uncheck the "Connect NAT on tunnel"
Check "Start with WAN"
[Save]
Nothing has to be changed on the Client 1 -> Advanced Tab
Open up the Client 1 -> Keys Tab.
Open up "ClientRouterKeys.txt" file you created earlier in the tutorial and cut/paste the certificates and key into the appropriate field.
ca.crt in the Certificate Authority box
Site2SiteClient.crt in the Client Certificate box
Site2SiteClient.key in the Client Key box
Don't forget to [Save].
Your done with the configuration. The moment of truth, on the Client 1 -> Status Tab, Click "Start Now"
Wait a few seconds and click on the "Refresh Status" link. Hopefully you'll see some bytes in the Value column.
From Site B, you should now be able to access Site A network resources and vice-versa.
Lets give the VPN a quick test. Still connected to Site B, open up the OpenVPN Server Configuration page on your Site A router @ http://192.168.1.1/vpn-server.asp. Hopefully you can see a successfully status page like the one below:
Cross Site Name Resolution
At this point your Site to Site VPN is setup, but you'll only able to access network resources via IP Addresses.
To access network resources via a friendly name, you'll need to do two things:
1) Setup static DHCP lease reservation for the network device (you don't want the IP address changing)
- Go to Basic->Static DHCP/ARP/IPT
2) On the opposite router, setup a static WINS/DNS entry for the same network device
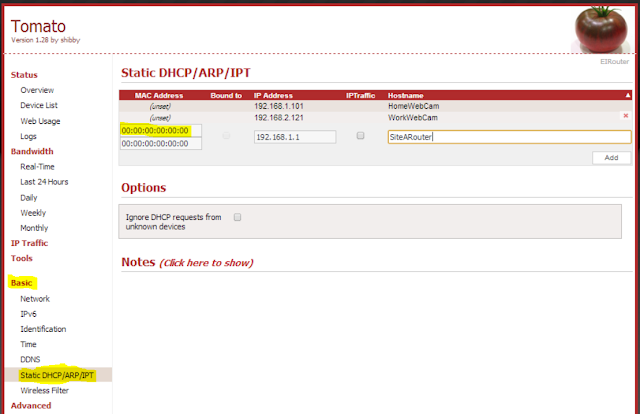
Go to Basic->Static DHCP/ARP/IPT. Typically the Static DHCP/ARP/IPT screen is for configuring static DHCP lease reservation, however you can use for static WINS/DNS entries also. The secret is to leave the MAC Address blank or with all zeros, "00:00:00:00:00".
In the screenshot below, on SiteB, I've setup a static hostname of "SiteARouter" so that I can access it via the friendly name versus the IP Address (192.168.1.1). From SiteB, I'm now able to access SiteARouter via name. Configure static hostname entries for all network resources you want to access on both your VPN sites.
That's it!! Enjoy.
Client to Site VPN
You should easily be able to add additional OpenVPN Clients (for Client to Site VPN) by generating additional RSA Certs/Key on your OpenVPN Server Router.
#Setup and initialize environment
PATH=/opt/bin:$PATH
cd /opt/etc/easy-rsa
PATH=/opt/bin:$PATH
cd /opt/etc/easy-rsa
source ./vars
./build-key Zoe-Laptop
./build-key Landon-Laptop
#Install SFTP so you can securely access your keys
#Location of keys = /opt/etc/easy-rsa/keys
#Connect as root
opkg install openssh-sftp-server
#scp is another alternative method to access your keys
[Tutorial] CentOS 6 OpenVPN Client - Connecting to Existing Site to Site VPN
Troubleshooting and FAQ:
- Watch my walk-through video
- Make sure the time is correct on both routers (NTP is setup, watch video)
- Check the logs
- Restore Default Configuration and start fresh (backup your current config, just in case).
Erase all data in NVRAM memory (thorough) @ http://192.168.1.1/admin-config.asp
Special Thanks to Shibby for the excellent firmware, the Entware Team, and Wasaga Computer's for their excellent blog (which is the original tutorial I used to successfully setup my first Site to Site VPN using TomatoUSB).
If you have any issues, have any questions or notice any mistakes, please don't hesitate to leave a comment. Your feedback will help me improve the tutorial and keep it up to date. Thank you.
./build-key Zoe-Laptop
./build-key Landon-Laptop
#Install SFTP so you can securely access your keys
#Location of keys = /opt/etc/easy-rsa/keys
#Connect as root
opkg install openssh-sftp-server
#scp is another alternative method to access your keys
Troubleshooting and FAQ:
- Watch my walk-through video
- Make sure the time is correct on both routers (NTP is setup, watch video)
- Check the logs
- Restore Default Configuration and start fresh (backup your current config, just in case).
Erase all data in NVRAM memory (thorough) @ http://192.168.1.1/admin-config.asp
Special Thanks to Shibby for the excellent firmware, the Entware Team, and Wasaga Computer's for their excellent blog (which is the original tutorial I used to successfully setup my first Site to Site VPN using TomatoUSB).
If you have any issues, have any questions or notice any mistakes, please don't hesitate to leave a comment. Your feedback will help me improve the tutorial and keep it up to date. Thank you.










Followed this to the letter. Having an issue with the client router crashing when I start the service. No log entries to see what the problem is. Any ideas where to look?
ReplyDeleteI have tried other tutorials with the same result of having the client router crash. Tried several builds of shibby and even bought a new Asus n66 and tried merlin's firmware.
FYI - Chris managed to resolve this issue himself. We're not clear on the root cause, so if you experience this problem please let me know.
DeleteThe OpenVPN client router configuration is trivial. My suspicion is it has to do with the copy/pasting of the cert/keys. Maybe a illegal character somehow got added, or you're missing a required line feed.
Or could it be over nvram limit? Did you configure more than one client?
DeleteYou very help me setting this and I really appreciate it. Could you tell me if you did some tests with an iphone client??
Deletethanks please reply or email me martin at mfdomotique dot com
I had the same problem of Chris... my mistake was to write under Client-Specific Options the tutorial's common name "Site2SiteClient" and not my cert's common name >> "Client".
DeleteI replaced "Site2SiteClient" with "Client" and all went smooth.
You have any recommendations for a script that can be used to monitor that status of the line and when marked as down to retry to reconnect?
ReplyDeleteThis would be useful if the OpenVPN server's connection would to go down. The script would trigger OpenVPN to retry to reconnect after x amount of time.
Hi Nick,
DeleteI believe this is built into the OpenVPN client. The OpenVPN client will automatically reconnect once the OpenVPN server is available again. I just rebooted my OpenVPN Server router yesterday and all my clients reconnected back just fine.
Qui
I don't think port forwarding on server is necessary.
ReplyDeleteMy client and server setup is almost same as yours, except the port forwarding part. Anyway, I can ping server lan from a host on client lan, but not from server to a host on client lan. Any idea how to fix that?
Hi Kevin,
DeleteThanks for your question.
The only port forwarding I have is "Forward UDP Port 1194 to your router internal IP @192.168.1.1" which is definitly required.
Server LAN to Client LAN routing is handled in the Advanced Tab of the OpenVPN Server configuration - the screenshot and section right before the Port Forwarding Section. Specifically the "Allow Client<->Client" and the "Push" based on Common Name, Subnet, Netmask.
Please let me know if that help resolve your issue.
I fixed my own problem. The problem was the windows firewall on Win7 host. Once disabled, it can be pinged.
DeleteI summarize things I did differently than yours:
* I used windows version of openvpn to generate the certificates/keys. It is much easier than installing optware/entware. Besides, it reduces the need for USB drive.
* I used jffs to store the ca/key files. Again, this relieves the need for usb drive. I used winscp to transfer ca/key files into /jffs/etc/openvpn
* USB drive is not needed. Although Tomato with USB provides many benefits, it is not a prerequisite for running openvpn.
* server firewall port forwarding of 1194 to server router itself is NOT necessary. I don't have it and mine worked flawlessly.
* even on the client router, do NOT use web GUI to paste the ca/key. Use winscp to transfer to /jffs/etc/openvpn/. Entering ca/key in web GUI will use up the tiny 32kb nvram. It may be OK if you only configure one openvpn client or server. But if you ever configure/enter them for another client or server, you are bound to exceed the 32k nvram limit, and your router will behave strangely, even restoring to default setup. It is better never use web GUI to store any ca/key files for openvpn, just to be safe.
Thanks Kevin for your feedback. The USB drive isn't required for the OpenVPN setup, however I find it more elegant to generate the keys on the router and it makes for a more easy to follow tutorial (cut/paste, minimal steps).
DeleteI understand some people, like yourself, prefer to generate the keys on their computer.
Using /jffs to store the keys to save nvram is a great solution.
I'll have to double check on the port forwarding. I'm confused how it would work without it. Did you start from scratch with a wipe of NVRAM? Any chance you might have some pre-existing IPTABLES entries?
Port forwarding is not needed to reach a server running on the router itself and listening on the WAN interface. Just like you don't need to forward port 22 for ssh into the router from WAN, or you don't need to forward port 8080(or 443) to reach the router web GUI from WAN. Openvpn client does not need the forwarded port 1194 to reach the openvpn server on the router from WAN.
DeleteI agree optware is really powerful and I am still learning it. But to use it properly, you need proper setup, like partitioning the USB harddrive with a swap partition and a ext3 partition (for optware and data). It is overkill if all you need is openvpn. Removing this setup opens up the possibility for all non-USB Tomato routers.
I want to stress the importance of my last point of it is better NOT to paste the ca/key contents directly into the web gui. Since it it very possible to exceed the nvram 32k limit. None of the Openvpn tutorials I found on the web mentions this, and I learned this the hard way. I turned on two openvpn servers and did not know it exceeded the nvram limit. The router ran OK for a couple of days, but one day, it restarted and some of my router configurations were lost. I took me a full week to troubleshoot, trying to restore the config, until I read online about this nvram limit problem.
@Kevin7890, just wanted to thank you for pointing out that the Port Forwarding section wasn't required. I've verified it and removed it from the tutorial.
DeleteI have this setup and can ping ip addresses from the either side.
ReplyDeleteI have server using domain family1.lan and client router using family2.lan. How can I ping host.family2.lan from the server lan? I tried using server=/family2.lan/192.168.1.1 in the dnsmasq settings of server gateway, but it doesn't seem to work.
Eddie,
DeleteGreat question on name resolution. Sorry, I don't have an ideal solution for you.
- you can always use a host file
- assuming you're on a windows network, on the OpenVPN Client network router, I set "WINS (for DHCP)" to point to the OpenVPN Server router IP Address.
I believe you're on the path to the correct/ideal solution with the dnsmasq settings. If you manage to get it to work, please share. Thanks
FYI - I just added a section on name resolution.
DeleteThank you so much for the awesome tutorial. Is there a way to route all the internet traffic through the vpn server? If I check my external IP it is still the one from the ISP
ReplyDeleteThe "Direct clients to redirect internet traffic" checkbox on the OpenVPN Server Configuration Server 1->Advanced Screen looks promising.
DeleteYou might want to look here also -
http://openvpn.net/index.php/open-source/documentation/howto.html#redirect
I assume the checkout will add the "redirect-gateway" directive to the OpenVPN Server configuration.
If you get it working please report back on how. Thanks
One way of accomplishing this is by adding the "redirect-gateway" option to the client configuration file. I usually have two configuration files on each client machine where one config uses that option and one doesn't.
DeleteI have everything setup correctly, but I am unable to reach any host on the OpenVPN server LAN from the client side, apart from the server itself. Any idea what may be going on here?
ReplyDeletePerhaps I should also mention that the OpenVPN server router is not the gateway for this network, but sits behind another router which is forwarding the VPN traffic to it.
DeleteSorry Ethan I can not help. Your configuration is out side the scope of the tutorial.
DeleteI've made that configuration work sometime ago by adding a new route to your gateway, that routes the OpenVPN subnet back to your OpenVPN server. If I remember correctly the problem is that the hosts on your LAN tries to respond back on requests from the OpenVPN tunnel, but sends the responses to your gateway which doesn't know how to properly route them onward. How to add this route to your gateway is device specific, but I hope you can find that information somewhere :-)
DeleteIt's me again... Wanted to set up a new site-to-site... Having troubles.
ReplyDeleteI noticed a couple of differences in the text from the video and whats posted on the blog. Not sure if that stuff matters. Anyway I have been cutting and pasting directly from this page. Here is what I have noticed.
The key sizes are being created at 2048 instead of 1024... Not sure if this matters.
After creating all of the certificates, outputting the the counsel does not work... Throws out an error. After a bit of poking around I discovered that the /opt/openvpn-easy-rsa/keys (keys folder) folder does not exist.
Any insight. Where would the keys be located?
Follow the blog. I would recommend that you start over from scratch.
DeleteThere are specific commands in the tutorial for changing the key size and creating the necessary folders which weren't properly executed.
#Set working directory and reduce key_size to 1024 in vars file
Deletecd /opt/openvpn-easy-rsa
sed -i 's:`pwd`:/opt/openvpn-easy-rsa:' ./vars
sed -i 's:KEY_SIZE=2048:KEY_SIZE=1024:' ./vars
Thanks for your quick response... Ran through this three more times today, exactly as shown in the guide.
DeleteStill doing the 2048 key size and the keys directory does not exist.... Here is what I see after I paste the final code into putty.
root@SiteARouter:/opt/openvpn-easy-rsa# cd /opt/openvpn-easy-rsa/keys
-sh: cd: can't cd to /opt/openvpn-easy-rsa/keys
root@SiteARouter:/opt/openvpn-easy-rsa# cat ./ca.crt
cat: can't open './ca.crt': No such file or directory
root@SiteARouter:/opt/openvpn-easy-rsa# cat ./Site2SiteClient.crt
cat: can't open './Site2SiteClient.crt': No such file or directory
root@SiteARouter:/opt/openvpn-easy-rsa# cat ./Site2SiteClient.key
cat: can't open './Site2SiteClient.key': No such file or directory
root@SiteARouter:/opt/openvpn-easy-rsa#
Hey Chris,
DeleteLooks like the openvpn-easy-rsa entware packaged changed a little bit which broke the tutorial.
I've updated it and just re-verified it.
Note that I removed the Port Forwarding Section as @Kevin7890 pointed out that it's not needed (I've verified this).
I really appreciate your persistence and letting me know that the tutorial is broken.
Give it a try again and let me know if you're still having any issues.
Qui
Golden! All is well... Gonna buy you some coffee..
DeleteI appreciate your attention to my posts.
Take Care!
Chris
Hey Chris, thank you for the generous donation! Glad to hear you got it working.
DeleteQui Hong:
ReplyDeleteI've taken the steps above exactly as shown -- with the exception of running "opkg update" in order to get the updated package list including OpenVPN ..
Everything works perfect. I can ping from SiteA to SiteB perfectly and vice-versa.
I'm having problems adding a SiteC .. We have 5 locations in our company and I'd like to add the additional sites to this VPN. Would you mind telling me which steps to replicate for each site? I created the additional Site2SiteClient keys (named after their client sites of course) and pasted them into the client router, along with the CA.crt. I've also added the client sites in the list with it's client subnet in the Advanced Tab on the Server router. When I enable it and save settings, it knocks down SiteB, even though SiteC's OpenVPN client never starts successfully.
Any clues on what I'm doing wrong? Thanks in advance ..
PS. Your instructions for Site2Site were spot-on. For TWO sites, this tutorial is golden.
Hi, great tutorial i managed to configure two tomato clients now. I think that the option of create NAT on tunnel should be enabled, at least for me is working like this.
ReplyDeleteThank you.
Not sure why you would want to use NAT on your tunnel. It should not be checked but if it's working for you great.
DeleteDid you try PueeVPN Nat firewall Add-on?
DeleteHi and thanks for the awesome tutorial. I haven't started yet as my routers haven't been delivered but I have one concern. I don't know if Entware is still available at http://wl500g-repo.googlecode.com/svn/ipkg/entware_install.sh
ReplyDeleteIf I put it into my desktop browser it prompts for a username and password. Can I use this instead?
http://entware.wl500g.info/binaries/mipselsf/installer/entware_install.sh
Used this guide:
ReplyDeleteSSH'd into router, used Linux based commands to generate keys, put server keys on USB stick in Server router(Site A), copied contents for Client Router (Site B) onto another USB stick and took with me to site B.
Note- Site A VPN service started and seemed fine- though wasn't connecting to B because it wasn't setup yet.
Got to Site B, pasted contents into VPN Tunneling -> Client -> Keys, started, and after a few moments the Router crashed(or so I thought). Lost Internet connectivity on Ethernet connected and Wireless connected machines. Lost connectivity to Router via Web GUI, Putty and WinSCP.
I rebooted Router at Site B via Power Switch, and still unresponsive. I pulled WAN Ethernet from Router and after a moment could connect to Router again. I cleared NVRAM(thourough), and started over.
Same thing happened. I've heard about the 32KB NVRAM issue with the ASUS RT-N66U router, but had upgraded original firmware to the 64KB before Tomatoing. Pulled WAN again, Router became responsive.
I SSH'd into and did a top and nvram show. Load was fine, had more than half of NVRAM available(and yes, was showing a sum of near 64). Plugged in WAN, and hit up arrow and Enter to continue to monitor stats before everything froze up.
I thought 'maybe it's the keys', 'maybe they're corrupt, or there's some line feed carriage return issue'(and I'm not 100% sure there's not), but when I edited the keys and removed parts, the VPN service just wouldn't start and Router and Internet never broke.
So I moved the keys from being pasted into Keys section of WebGUI VPN Tunneling ->Client ->Keys to the JFFS(enabled and formatted first) via SCP, then put those certs and key paths into the VPN Tunneling ->Client ->Advanced ->Custom. Same behavior.
I see a couple things in there I'm not sure about:
1. I see the DDNS address not being resolved XXproductionXXcom
2. I see the private IP addressing scheme of the office production site 10.1.10.0 from behind this 192.168.2.0, which tells me a connection is being made.
3. I later see WAN down, is that when things go crashy?
Unless it's something I did wrong in the configuration, here's one more thing that may be contributing:
Client Site B has DSL, and it's not good. I did a speed test and got about 2.5 Mbps down and between .25 and .70 Mbps up. Could it be that the Internet is so bad that the VPN is using every morsel of bandwidth/throughput and clobbering itself? If so, is there a way to throttle it, or scale it down so that it continues to function steadily albeit slowly?
I welcome all thoughts and hypothesis before I take another swing at it tomorrow.
I setup OpenVPN on my E3000 Linksys with Tomato. Everything seems to be working EXCEPT I can't access my NAS shares (I can ping the NAS just fine). Any ideas? I'm using the OpenVPN client on Android and have tried a number of file managers with the same result.
ReplyDeleteI truly enjoyed reading your post. we will bookmark your blog for future refernece. I want to encourage one to continue your Great post. vpn service
ReplyDeleteI'm trying to setup a dual VPN system on my Linksys TomatoUSB router. What I currently have is a Dedicated IP VPN that handles my outbound traffic from behind the router, and that works fine. If I disable that connection and enable my local VPN server, I can connect to that as well from outside the network. What I want, however, is the ability to connect remotely to the router, and then have that remote traffic get routed through my dedicated ip over vpn.
ReplyDeletePlease help.
DeleteWords fail me. Not only is this wicked-cool, but it works fabulously! After following your recipe, (with the exception of the broken link to entware install), my two routers were connected. Now I can access my Drobo5N like it was on my LAN! Sweet!
ReplyDeleteThanks so much for posting this.
Hi, I am currently working through this tutorial and have run into this broken link. Would you be able to provide me a working link? Thanks in advance!
DeleteI think that thanks for the valuabe information and insights you have so provided here. best vpn services
ReplyDeleteI really appreciate this wonderful post that you have provided for us. I assure this would be beneficial for most of the people. VPN China
ReplyDeleteM friend this is an excellent article / tutorial. I have a little problem that you may help me if it is possible. I can ping from client router server LAN , but I cannot ping from client PC's any host of server LAN including the server Router .
ReplyDeleteWhat am I missing ?
Thank you
It is a very informative article. totally loved it. I would like to discuss it with you people and the USA VPN.
ReplyDeleteReally it was an awesome article...very interesting to read..You have provided an nice article....Thanks for sharing.. routers internal ip
ReplyDeleteNice read up, really informative article. I am using a UK VPN
ReplyDeleteto hide my identity for hackers.
A monetary consultant, transfer funds to or from an Edward Jones account online. https://edwardjoneslogin.org They can sign up for as well as utilize completely free at and net link.
ReplyDeleteYou have got performed a splendid method on this article. It’s very readable and rather sensible. you have got even managed to make it comprehensible and smooth to study. you have got some actual writing understanding. Gmod game
ReplyDeleteCreating a blog can appear difficult for many people, even though for some individuals it's an simple process. Nevertheless, a very important factor that everybody shares in common is that they are searching for ways to improve their blog and attain incre.cheap shoes in Pakistan
ReplyDeletenice blog...
ReplyDeleteLinksys Login Net
Mostly i use VPN for torrenting because in my region torrenting is pretty shady activity. Hoowever i am using ExpressVPN and it is working aweosme.
ReplyDeleteawesome blog and excellent information on vpn. I recommend you to try Fastest VPN
ReplyDeleteThe best Singapore VPN is ivacy. I am using it to by pass geo restricted content online.
ReplyDeleteThanks for setting aside the opportunity to talk about this, I feel firmly about it and love adapting more on this point.
ReplyDeleteGo to Uk Writing Experts
What a great feed!
ReplyDeleteAmazing enough.
Plus, I recommend you to try Reasonable Vpn Services by Best Vpn Deals. I am so satisfied with the services. hope you'll get the same feels.
You'll need to add a route back to your local IP address via the normal ethernet interface (i.e. not the tunnel). 'ip route add 2001:db8:beef::1234 via fe80::1 dev eth0' should do it, substituting your real IP address and your default gateway's IP address.
ReplyDeleteThis will mean all traffic to your local IP address will bypass the VPN. Them's the breaks.
Read ExpressVPN review as they help out in setting up OpenVPN quickly https://www.criticthoughts.com/vpn/expressvpn-review/
You'll need to add a route back to your local IP address via the normal ethernet interface (i.e. not the tunnel). 'ip route add 2001:db8:beef::1234 via fe80::1 dev eth0' should do it, substituting your real IP address and your default gateway's IP address. This will mean all traffic to your local IP address will bypass the VPN. Them's the breaks.
ReplyDeleteRead ExpressVPN review as they help out in setting up OpenVPN quickly
You have done a great job on this article. It’s very readable and highly intelligent. You have even managed to make it understandable and easy to read. You have some real writing talent. Thank you. visit website
ReplyDeleteJust admiring your work and wondering how you managed this blog so well. It’s so remarkable that I can't afford to not go through this valuable information whenever I surf the internet! privatnost online
ReplyDeleteThe most inspiring stuff commonly is probably the most dull or boring concern. a single rooster may not be in the same woody plant strip very long, and also the pets within the pine is a kind of weight, always want to consult the next stars, the particular fowl because the plants are really hesitant to facial expression an equal beautiful places day by day. www.lemigliorivpn.com
ReplyDeleteThe article you have shared here very awesome. I really like and appreciated your work. I read deeply your article, the points you have mentioned in this article are useful gizlilikveguvenlik
ReplyDeleteThis content is written very well. Your use of formatting when making your points makes your observations very clear and easy to understand. Thank you. privacidadenlared
ReplyDeleteGood composed article. It will be steady to any individual who uses it, including me. Continue doing what you are doing – can'r hold up to peruse more posts. diadiktiokaiasfalia
ReplyDeleteAmazingly accommodating post. This is my first time i visit here. I found such an extensive number of captivating stuff in your blog especially its trade. Genuinely its unprecedented article. Keep it up. internetprivatsphare
ReplyDeleteI am unquestionably making the most of your site. You unquestionably have some extraordinary knowledge and incredible stories. vpn
ReplyDeleteYou have done a great job on this article. It’s very readable and highly intelligent. You have even managed to make it understandable and easy to read. You have some real writing talent. Thank you. diebesten vpn
ReplyDeleteI want you to thank for your time of this wonderful read!!! I definitely enjoy every little bit of it and I have you bookmarked to check out new stuff of your blog a must read blog Netflix VPN
ReplyDeleteI'm seeking to setup a twin VPN system on my Linksys TomatoUSB router. What I currently have is a Dedicated IP VPN that handles my outbound traffic from at the back of the router, and that works satisfactory. If I disable that connection and permit my local VPN server, I can hook up with that as nicely from outside the network. Avail 15% Discount On Custom Essay Help
ReplyDeleteWonderful blog.. Thanks for sharing informative blog.. its very useful to me.
ReplyDeleteVisit: Top Essay Writing Service UK
I have read your blog it is very helpful for us. I couldn't find any knowledge on this matter prior to. I am very thankful to you for sharing this type of article here. If anyone looking for the best dedicated ip vpn service, Visit vpnshazam.com
ReplyDeleteExcellent .. Amazing .. I’ll bookmark your blog and take the feeds also…I’m happy to find so many useful info here in the post, we need work out more techniques in this regard, thanks for sharing. vpnveteran
ReplyDeleteIt's great to read out this tutorial on Site to Site VPN, insightful and informative as well. I m thinking to buy PureVPN and will do the same.
ReplyDeleteAustralian open on Kodi is the easiest way to watch the event live. Here are some simple steps to get VPN and live stream links up and running.
ReplyDeleteYes. I also think that you have the correct ability to create the most important results and then make it super easy for yourself to get things done in the right niche and proper way. If you think that there is nothing more important than the people in the society the essay writers uk
ReplyDeleteGet FastestVPN as your UK VPN for the best speed and P2P optimized servers for just $0.83/month as they are offering 92% discount on 5-year plan
ReplyDeletewow, great, I was wondering how to cure acne naturally. and found your site by google, learned a lot, now i’m a bit clear. I’ve bookmark your site and also add rss. keep us updated. vpnveteran
ReplyDeletegiven article is very helpful and very useful for my admin, and pardon me permission to share articles here hopefully helped :
ReplyDeleteCara mengobati ginjal mengecil
Obat gagal ginjal ampuh
Cara menghilangkan varises di kemaluan
Cara menghilangkan bopeng
Cara menyembuhkan ispa
Obat pengapuran tulang tradisional
Cara mengobati flek paru paru pada anak
This comment has been removed by the author.
ReplyDeleteInteresting read this. I have been using Ivacy's USA VPN server to access US Netflix Libraries without any hassle. Keep sharing!
ReplyDeleteComing in at a slightly more affordable price than the P600, the Advanced Platinum Series P450 still offers fantastic quality to cannabis growers. The only difference is that this model has 450 watts rather than 600. Naturally, which unit you choose is down to the size of the crop you want to grow. You can expect 2-3x the intensity of other lights due to the high PAR output per watt. In order to flourish, crops really need the full light spectrum.
ReplyDeleteHi,
ReplyDeleteIf you wont access any particular site, can easily access by using world Top FastestVPN If you want VPN services like VPN for Linux or router so please check out the FastestVPN for the awesome speed and P2P optimized Servers for just $0.83/month as they are offering 92% discount on 5-year plan
Thanks for sharing this article.
ReplyDeletehttp://site11513685.23video.com/kongsgada-og-klubbgada
http://icalshare.com/calendars/37
https://terrorandbullies.omeka.net/items/show/45
https://www.amazonforum.com/forums/digital-content/prime-video/493428-app-not-working-on-lg-tv
http://csalco.bravejournal.com/entry/21877
Your post is very helpful to get some effective tips to reduce weight properly. You have shared various nice photos of the same. I would like to thank you for sharing these tips. Surely I will try this at home. Keep updating more simple tips like this. meer informatie
ReplyDeleteThanks for sharing such a nice Blog.I like it.
ReplyDeletemcafee.com/activate
norton.com/setup
I couldn't find any knowledge on this matter prior to.Also operate a site and if you are ever interested in doing some. https://internetetsecurite.fr
ReplyDeleteGetting unwanted errors while working with Quicken software - instant get n touch with 24x7 Quicken Support Desk.
ReplyDeleteQuicken ol-301-a
Quicken error code cc 501
Quicken error code cc 502
Quicken cc-506
lampung
ReplyDeleteiPhone
Maspion
Makalahandroid
Natar
oppo
Service HP
lampungservice.com
QuickBooks Pro and Premier have their respective advantage and disadvantage and are suitable as per their business needs. This blog will help you to understand the complete difference between QuickBooks Pro and premier. QuickBooks Pro is a starter edition of the software. QuickBooks Premier is a level up from QuickBooks Pro because of some additional features.
ReplyDeleteQuickBooks File Doctor
QuickBooks h505 error
QuickBooks multi-user mode
TurboTax is a highly acknowledged software for tax preparation. It helps the users in preparing for tax cuts. TurboTax team will help you with the on-going issues that you come under your way. Our service base consists of Issues with Installation, Tax Return Errors, Update Errors, Raising Your Credit Score, Counselling in instances of an audit, Every detail reviewed etc. You can contact us at Turbo Tax Customer Service phone number 844-616-4459.
ReplyDeleteQuickBooks is a huge accounting software with numerous features. QuickBooks Point of Sale is one of them. Users often face error initializing QuickBooks Point of Sale application log due to the compatibility of two or more software, damage in windows system files etc. There are various methods through which you can resolve the error effectively.
ReplyDeleteMcAfee Support Number
ReplyDeleteAvast Support Phone Number
Norton Customer Service Number
Malwarebytes Support Number
QuickBooks add-on software suggestively elevates the features of QuickBooks accounting software. QuickBooks add-on is a program or software that boosts the functions of QuickBooks financial application program. Also, a QuickBooks add-on can be defined as a program that adds much new functionality to the QuickBooks accounting software.Totally free QuickBooks support service is offered by a cloud hosting service and application hosting vendor. QuickBooks add-ons hosting service provider’s support team fully assist you. Visit : Quickbooks support
ReplyDeleteDial Quickbooks Online Customer Service Number +1-888-412-7852 for instant fix QuickBooks online banking issue from certified technical experts round the clock.
ReplyDeleteIf you are man belonging to the upper strata of the society, then we would like to mention that our agency does have some of the best and most well educated Ramnagar call girl for exotic companionship. Whether it is a top notch party or a late night event, ask our executives to accompany you. They will happily continue to spell their magic and make things really interesting. Gone are days of loneliness and boring activities. We have some of the raunchiest divas in store for you. They will make each and every occasion look attractive and enjoyable in your eyes.
ReplyDeleteOn the off chance that you need to have a little flavor, you've discovered recently the correct young lady. On the off chance that you need some vigorous love, I'm all yours. On the off chance that you are intending to get again into the dating, yet no thought how to begin, we can rehearse. Ideally, it is only the start of our story together. Nainital escort service come to us of their own accord and we support them in their goals and endeavours.
ReplyDeleteAre you searching for top class and sexy call girl in Noida for a romantic dinner date or tonight party? We are providing top class horny and busty Noida call girl for fulfilling your erotic pleasure. Just call Kajal Roy and reserve your meeting. Our high profile Greater Noida call girl provides all types of services. Greater Noida escort service agency is very popular in young people. Hire high profile call girl in Greater Noida and enjoy your party like a playboy and get pleasure.
ReplyDeleteGreater Noida call girl ## Noida call girl ## Ghaziabad call girl ## Nainital call girl ## Indore call girl ## Bangalore call girl ## Goa call girl ## Crossing republik call girl ## Pune call girl
Expert in experienced professional accounting recruitment by cheapassignmenthelp.co.uk, and there are academic degrees such as undergraduate, masters and PhD in various disciplines of accounting so that they can provide an innocent service. Experts offer original and unique content for homework and also provide very useful editing and research services for students.
ReplyDeleteA student, who wants to rent accounting homework assistance, can easily expect the following types of services from our specialists.
A clear, concise and well written homework that confirms to the standard and quality of the candidate.
A plagiarism free content that will be exclusive in nature.
Unlimited editing can be requested by the experts so that it is up to the mark that a student is looking for.
Multiple revisions can also be requested.
All these services can help a student achieve the quality of homework, which helps in understanding the student’s goal by providing such a service and therefore, obtaining good grades.
You can reach us at-
Email:- ozpaperhelp@gmail.com
https://www.ozpaperhelp.com/
https://www.cheapassignmenthelp.co.uk
https://www.freeassignmenthelp.com
https://cheapassignmenthelp.blogspot.com/
Whatsapp :+61-451442632.+91-7503070001,+44-7437875635
We have been providing the best essay services to the students around the globe and in the UK. We make sure that each and students receive customised Law Essay Help, distinct from one another, at the lowest prices possible.
ReplyDeleteWe at Law Writing have been providing services to the students for many years. The content we compile and produce is authentic. You can contact our customer care representative and feel free to submit your order at the lowest prices.
ReplyDeleteThe sexiest Nainital escort service Number divas and escorts are conceived in . Their way towards life towards bliss towards keeping up their benefits is awe-inspiring. Escorts Girls Nainital presents you with a portion of the hottest and perfect succulent divas on earth that are searching for great looking refined men to fulfill their dreams in cot. Has torrential slide of customers who reach us time to time for blasting with a hot escort. We are the command escort agency of this town. We have assortment of alternatives for you.
ReplyDeleteI am available mostly in Nainital call girl Service but I would be delighted to join you for weekend to any place in India or if you want me to travel with you for holiday out of India than also I am available but if you wish so.
Interested Services:
Call girl in Nainital
Nainital call girl
Escort service in nainital
Nainital escort service
ReplyDeleteIts an interesting post with a clear concept and very useful for me and I want much more post from your great post. Keep it up such a great posting like this...
Oracle DBA Training in Chennai
best oracle dba training in chennai
Spark Training in Chennai
Oracle Training in Chennai
Job Openings in Chennai
Placement in Chennai
Soft Skills Training in Chennai
JMeter Training in Chennai
Tableau Training in Chennai
Oracle DBA Training in Porur
Raheja Mall
ReplyDeleteGo through an entire night with our attractive call young ladies in Nainital. Get a sexual involvement with our hot young women. They all are made for you and sitting tight for you. Sonali is looking each time men who the fuck her like a puppy (who has bunches of vitality to do sex). Her boobs dependably anguish for suck by you. You can book our Nainital escort service five star lodging or all over Nainital Hotels. Our Call girl in Nainital are accessible in each Nainital range’s Hotel for entire night administration. We give best costs and protection of our young women and customers in Nainital .
ReplyDeletequickbooks error 3371, Status Code -1 QuickBooks could not load the license data. This may be caused by missing or damaged files. This error is usually caused by one of the following: Outdated Windows operating system or an anti-virus program that quarantines some QuickBooks Desktop files.When you face any sort of technical problems with your QuickBooks software, you can easily call our QuickBooks contact number and leave the rest to us. We are here to reach for any technical help through a telephone number, emails, and live chat. Our specialist can easily answer all of these questions and complete the initial setup and installation in a timely manner.We have a high equipped technical specialist who can handle all kinds of problems side by side, at the same time.for more information call at 1800-470-6903
ReplyDeleteWhile picking out the custom packaging for your product or service, you have to keep the price range in mind as it’s not one item or one-time buy. A fancy and also costly box can make you seem like it’s the only one however while getting it, you have to analyze the budget on larger level specially when you are just in the beginning of custom packaging. pie boxes custom pie boxes click here learn discover check my site printed pie boxes wholesale pie boxes learn more One inappropriate action might cost you much.
ReplyDeleteDoes It Signify Your Brand Proper?.
If your QuickBooks program is experiencing any sort of technical difficulties then, contact on the Quickbooks support Phone Number for instant resolution.
ReplyDeleteQuickbooks error code 3371 appears on the screen, the user fails to open the company files. Repairing doesn't resolve the issue. for More Information click below :
ReplyDeleteQuickBooks Error 3371 | QuickBooks online error 102 | QuickBooks Error 1712 | QuickBooks Error 1603
Thank you for investing your valuable time for writing such an amazing post for all of you.
ReplyDeleteQuickBooks Error Code 1321
QuickBooks Error Code 9000
Microsoft Office is a complete instrument for home and office. It is exceptionally helpful for understudies and working expertly as it incorporates such a
ReplyDeletesignificant number of work area application like Microsoft Word, Microsoft Access, Microsoft PowerPoint, Microsoft OneNote, Microsoft Excel and numerous others.
Need Help Click Here. www.office.com/setup.
It has been seen that many sorts of antivirus reduce the speed of the system. In general, users think that this might
have happened due to antivirus. Yes, this could have happened because of the same. But, as a lay user, what would you do?
Will you remove the antivirus and make your computer prone to viruses and malware. Sometimes, this may happen with Norton
antivirus as well. You do not need to remove the antivirus; rather you should call the experts of Wiz Customer Service.
They are highly experienced in fixing the speed problem of the computer occurred due to antivirus.
Need Help Click Here. www.norton.com/setup
If you are facing issue and errors in Quickbooks then Connect with us at our toll-free and 24/7 QuickBooks Support +1 888-547-2184 and get all the solutions at your fingertips. QuickBooks Support is equipped with highly secure and latest technology remote access tool and Expert technicians. Our qualified team holds a specialization in managing and handling the difficult QuickBooks problems in less span of turnaround.
ReplyDeleteQuickBooks Support
QuickBooks Number
Really a nice blog and great kind of information is provided by you. Thanks a lot for sharing.
ReplyDeleteQuickBooks related issue and Error then contact QuickBooks Customer Service Phone Number and QuickBooks Contact for solving the QuickBooks accounting Software.
I have read several just right stuff here. Definitely price bookmarking for revisiting. I surprise how so much attempt you set to make such a great informative website.
ReplyDeletehttps://voodesty.com/canon-camera-with-flip-screen/
https://voodesty.com/sony-vlogging-camera/
https://voodesty.com/best-digital-camera-under-300/
https://voodesty.com/best-running-shoes-under-500/
https://voodesty.com/best-vlogging-camera-that-youtubers-use/
https://voodesty.com/best-electric-scooter-for-climbing-hills/
Hello there, just became aware of your blog through Google, and found that it is truly informative. I'm going to watch out for brussels. I will be grateful if you continue this in future. Numerous people will be benefited from your writing. Cheers!
ReplyDeleteCanon With Flip Screen
Sony vlogging camera
Best Digital Camera Under 300
Best running shoes under 500
best vlogging camera that youtubers use
Best Electric Scooter For Climbing Hills
El diseño de calzado para correr CloudTec de fat On utiliza reglas relacionadas. Zapatillas Air Jordan 5 baratos El efecto puede ser una bota de apoyo, ligera y más resistente, al igual que Trend Generation y Trend Prediction. En 2016, Mizuno introdujo la ingeniería de zapatos o botas de educación Cloudwave dentro de Trend Riders 20, cuando el menú de tendencias presenta una geometría cóncava específica para poder colocarse debajo con el tacón alto. Idea principal.
ReplyDeleteThanks for your fabulous post! I enjoy while reading your post, you happen to be a great author. When I am free than reading your blog. I want to encourage yourself to continue to share fabulous posts, have a nice day! We also provide QuickBooks Enterprise Support for QuickBooks User.
ReplyDeleteElettronico. In relazione al jogging, tutti i tipi di cose da prendere partecipano alla tua attuale biomeccanica, peso, il contatore di cui tutti sono alimentati oltre alla forma di piedi da ginnastica, le sneaker sembrano questo significa che nessuna sneaker andrà Nike scarpa uomini sicuramente bene con ogni singola forma di atleta . Uno dei numerosi problemi che abbiamo scoperto nel corso dei secoli nel rendere le testimonianze di sneaker come allenatore di sneaker per ottenere sneaker RW sarà il mezzo che ciascuno dei nostri multilivelli che coinvolge gli sportivi si mostrano.
ReplyDeleteYou are assured of one thing that the range of prices that you have to spend for gaining the services of the Call girl in Ramnagar is not much at all. What these women try to maintain their highest level of service quality in order to allure the customers more and more. That is the reason our agency has been able to be one of the finest reputed one in the midst of all the others in the entire industry.
ReplyDeletesåvel som at bruge et holdbart fodtøj til rådighed, materialer. Denne særlige magt tilbage er faktisk meget let synlig fodtøj online butik på Nike Air VaporMax 2019 sko udsalg næsten alle opererer af uformelle fodtøj miles. Nogle ting helt nye atletiske sko med denne ajourførte udgave fra fodtøj, golfboldfodtøj Altra yderligere manuelle Sengeskinner mod overfladen af mellemsålen rundt om for at hjælpe med at styrke den faktiske rygshæl samt give en lille ramme via din egen fremgang.
ReplyDeleteGreat post, and great website. Thanks for the information! best travel laptops in 2019
ReplyDeleteNiezależnie od tego, Butów Nike Air Max 270 męskie czy masz do czynienia z konwencją uliczną, czy nawet po prostu odkryłeś, że działa lokalna strefa rekreacyjna 5K, najważniejszym pakietem, którego potrzebujesz, jest właściwie zestaw najlepszych butów sportowych obuwia instruktażowego na krok. autokary operacyjne, które najlepiej pasują do Ciebie obuwie damskie, a także cel.
ReplyDeletevermeld elk modelbedrag, hier is de volgende technologie UltraBoost SAINT. De specifieke laars Schoenen Under Armour RailFit 1 goedkope biedt opmerkelijke handvol aanpassingen: vooral, er waren slechts een paar schoenen of laarzen op de markt, kleine aanpassingen voor de hogere, maar we identificeerden deze allemaal om het pak te vergroten en ook te voelen met de laars. Adidas gebruikte sterkere steken door middel van herenschoenen of laarzen de specifieke middenvoet om een beter pak te krijgen. Bovendien sloot het de bijzonder dikkere plastic-type supp.
ReplyDeletekaikki elinvoimaisuus palaa takaisin, ja myös tämä taso lasketaan yhdessä poikittaisten urien kanssa yleisen joustavuuden lisäämiseksi. Se on todella upea vaihtoehto lenkkeilijöille, jotka ostavat kenkiä tukevan matkan, ja lisäksi mahdollistavat, että niillä on polku. Erityinen Trend Darkness Fila Disruptor II tennarit halvalla tulee valon ympärille, voivatko kengät tai saappaat ohuempia päätelmiä Mizunon turvallisuudesta kengän tai saappaan suhteen. Se on todella melko neutraali ohjaaja, joka antaa kaikille lempeän, taitava jalkan. merkityksessä.
ReplyDeleteNezávisle na jasné vnitřní alternativní levné obuvi nebo botách. E. Ať už pracujete na fitness běžeckém pásu, můžete dokonce získat zimní běžecké boty za každého počasí a také během jednotlivých podzimních zimních období určitě řídit jednotlivé ulice. Práce v zimních týdnech může snadno zvýšit vaše současné aerobní zdravotní pojištění a v důsledku toho sportovní aktivity boty nebo boty vám umožní menší množství náchylné k zdravotním problémům boty. Práce Under Armour Highlight Delta tenisky může být mocným způsobem.
ReplyDeleteThe LojiQ is one of the best and trusted Website Development Company in USA, We offer Web Design and Development, Mobile App Development, eCommerce website development and Responsive, SEO Friendly Web Designing and development websites and Application.
ReplyDeleteWebsite Design and Development Company in USA
web design company in usa
website development company in usa
best digital marketing company in usa
amelyben elkészítette az adott háromcsíkos emblémát, és alternatívaként karcsúbb és még rugalmasabb anyagmodellekkel is utazott, hogy csökkentsék az olcsóbb cipőket vagy csizmákat, és az ingerlékenység miatt lehetőség van cipő vagy csizma megszerzésére, amint lábad. hajlani. A tesztelők megfigyelték, hogy a csomagtartó egy 50% -os méretű, de a nagyobb lábujjakkal Caterpillar Swingshift cipők bolt az emberek imádták azt a fölösleges területet, amely más népeket egyenesen lefelé mérve biztosított
ReplyDeleteThere are such a large aids of advantages of nursing assignment help online assistance. We should talk individually about the advantages of web based nursing assignment service .
ReplyDeleteThe LojiQ is a leading website internet marketing and best SEO company in USA. We will create a unique seo strategy to get more ROI and increase your business sales with Seo expert. Our Seo expert make effective strategy building for promote your business online with result oriented, That Give Results.
ReplyDeleteThe LojiQ is a leading website internet marketing and best SEO company in USA. We will create a unique seo strategy to get more ROI and increase your business sales with Seo expert. Our Seo expert make effective strategy building for promote your business online with result oriented, That Give Results.
ReplyDeletebest seo services company in usa
best seo company in usa
Pixels is a web and logo design agency which provide professional logo design services in USA & all around the world. We dedicate our services in crafting the best design for logos and websites at affordable prices. Explore our professional website for a high-profile business or a custom logo design for a small bakery shop, we provide tailor-fit solutions and provide individual attention to every design-related query. Our approach is to craft contemporary and visually-aesthetic designs to meet modern marketplace standards that too at affordable prices, our Logo Design Services in the USA are authentic and without any compromise on quality.
ReplyDeleteQuickBooks has changed the way business was done decades ago. The support team at QuickBooks Phone Number Support +1(800)986-4591 manage QuickBooks Error 3371. This excellent product has made a significant contribution to the growth and development of various companies around the globe. For more visit: https://tinyurl.com/w993rv7
ReplyDeleteLojiqbooks providing you 24X7 service for all possible QuickBooks issues and errors from our quickbooks accounting services. QuickBooks accounting system is one of the top accounting software that has integrated all featured such as payroll, accounting, pay check calculations, tax calculation, leave management, retirement benefits, healthcare, deductions and more. Lojiqbooks Service team is is available 24X7 and consist of professional, QuickBooks certified Pro-Advisors with highly skilled and possess problem-solving tactics.
ReplyDeletequickbooks services
A debt of gratitude is in order for putting aside the chance to discuss this, I feel immovably about it and love adjusting more on this point.
ReplyDeleteGo to task helpsassignment helps
Will you be expected to participate? Not at all! we'll choose the simply from any location, be it within the yard, basement, or at the top, we'll pay attention of the loading and once done, sweep the place wherever the trash was situated. going your premises higher than we tend to found it's our greatest policy!
ReplyDeleteJunk Removal Glassboro | Carpet cleaning in South Orange County | Fireplaces Oakville | Microblading Oakville | Retirement Planning in Orlando
ReplyDeleteVery nice and informative blog click here QB Support Phone Number 800 and for more detail dial on 800-901-6679
Very nice and informative blog click here QB Support Phone Number 800 and for more detail dial on 800-901-6679
ReplyDeleteVery nice and informative blog click here QB Support Phone Number 800 and for more detail dial on 800-901-6679
Very well explained and informative blog click here for
ReplyDeleteQuickbooks Payroll Support Phone Number and for more detail dial on our support number 800-901-6679 to get the solution
Can I simply say what a comfort to find someone that genuinely understands what they are talking about on the internet. You certainly realize how to bring an issue to light and make it important. More and more people should check this out and understand this side of the story. It's surprising you aren't more popular given that you certainly have the gift.
ReplyDeletehttps://kbcgameshow.biz/
ReplyDeleteترجمه تخصصی مدیریت و ترجمه تخصصی MBA ترجمه تخصصی مدیریت و تمامی گرایش های وابسته به این رشته و انواع خدمات دیگر توسط تیم ترجمه آنلاین
Nice and well explained blog click here for QuickBooks support phone number and for more detail dial on our support number 844-908-0801
ReplyDeleteNice and well explained blog click here for QuickBooks support phone number and for more detail dial on our support number 844-908-0801
ReplyDeleteVery nice and well explained blog click here for QuickBooks POS support phone number and for more detail dial on our support number 844-908-0801
ReplyDeleteNice and very informative blog click here for
ReplyDeleteQuickBooks POS support phone number and for more detail dial on our support number 844-908-0801
ReplyDeleteOur cute iphone xr cases is here to perfectly complement your iPhone XR’s unique color.
همانطور که مشخص است طراحی فروشگاه اینترنتی دیجی کالا توسط تیم شیراز سان انجام پذیرفته است. جهت طراحی فروشگاه اینترنتی آنلاین می توانید به تیم حرفه ای شیراز سان اعتماد نمایید. جهت اطلاعات بیشتر می توانید به وب سایت ما سر بزنید
ReplyDeleteI appreciate your post, Please Keep posting with more information… https://raybaby.us/technology
ReplyDeleteGreat information, thanks for sharing with us. Get the amazing website designing services by OGEN Infosystem in Delhi, India.
ReplyDeleteWebsite Designing Company in Delhi
I blog quite often and I seriously thank you for your content. This great article has truly peaked my interest. I am going to take a note of your site and keep checking for new information about once per week. I opted in for your Feed as well Online Dissertation Help UK
ReplyDeleteNice Blog Post. Really I got rich information for what I was searching.
ReplyDeletehttps://www.rozayraw.com/member/googleadultseo
http://talktoislam.com/user/googleadultseo
https://care-to-collaborate.com/members/googleadultseo/profile/
https://my.stuff.co.nz/profile/googleadultseo
http://www.oneplatter.com/members/googleadultseo/
https://www.meneame.net/user/googleadultseo
https://kubuckets.com/user/googleadultseo
https://www.relmaxtop.com/users/googleadultseo
Please check it out this website Best Tech Blog. This website provide you Benefits of Data Analysis web scraping and data extraction tools information and much more so visit tectiko blog and view your favourite tech information.
ReplyDeleteInteresting blog post, I always appreciate good quality content stuff.
ReplyDeletehttps://www.designkit.org/profiles/267359
https://www.iexplore.com/users/6495
http://www.usedtruckmountsales.com/author/chennaiescort/
https://www.linkhippo.com/author/chennaiescort/
https://www.northcyprusadvertiser.com/author/chennaiescort/
http://speedshop.rpm.tv/author/chennaiescort/
https://www.openstreetmap.org/user/Escorts%20Chennai
https://www.mql5.com/en/users/escortschennai
Contact to WordPress plugin Issue
ReplyDeletePurchasing plugin and Setup in WordPress is not easy task if you are looking help and assistance contact 247wpsupport experts. Who is always here to guide you with all the tasks which need to run a successful WordPress blog? Get assistance any time of the day on our WordPress Customer service at & 1 (844) 589 2165 and get instant solution,
https://www.247wpsupport.com/wordpress-customer-services/
Microsoft Office installation is essential tool for any PC inside this generation. It provides quite useful tools such as MS-Word, Excel and PowerPoint that are crucial for creating your task quite easy associated with company. This attribute makes Office.com/setup one of the greatest software bundle.
ReplyDeleteOffice.com/setup
Guarantee you have leap forward Operating System presented on your device.
ReplyDeleteIn case your system has some different Antivirus or security structure presented then uninstall it.
This can disturb while downloading and presenting Webroot.com/safe.
visit:
www.webroot.com/safe
Nice Blog ! We offer a wide range of plans you can choose from according to your needs. Call our toll-free QuickBooks For Mac Support Phone Number 855-907-0406.
ReplyDeleteAOL is an advanced email sending and receiving tool used for email services with security and safety you can download aol desktop gold and enjoy their services like emails services, music, news , internet browsing, etc
ReplyDeleteVery well explained and informative blog click here for
ReplyDeleteQuickBooks Support Phone Number for know more about QuickBooks dial on our support phone number 844-908-0801 to get the solution of all QuickBooks issues and error
Very well explained and informative blog click here for
ReplyDeleteQuickBooks Support Phone Number for know more about QuickBooks dial on our support phone number 844-908-0801 to get the solution of all QuickBooks issues and error
Thank you for this wonderful information looking forward for more. I am proadvisor in QuickBooks Software. If any problem related QuickBooks software and support. Then visit my Blog:
ReplyDeleteQuickBooks Activation Not Working Error Occurs
Create Journal Entry in QuickBooks Online
Set up QuickBooks Desktop on a Mac using Parallels
QuickBooks is an exemplary accounting software that give eminent benefits to the user. Perform all accounting tasks easily that involves managing of expenses, inventory tracking, estimating payroll, etc. Gain valuable assistance regarding your issues & query with QuickBooks support Phone Number Washington 833-780-0086. Avail instant effective solution from our QuickBooks experts. For More Visit: https://truecarecounsellingservices.com/quickbooks-washington/
ReplyDeleteRemarkable post! I really savored the experience of getting it. Keep sharing such articles. Envisioning acquire from you.. my crm system
ReplyDeleteThanks for talking on this topic, and shared to global. If are you using accounting software, Choose the best tools Sage 50, sage peachtree, sage payroll, sage quantum, sage one, etc.
ReplyDeleteDesire you will keep offering incredible substance like this even more consistently. I feel a regularly expanding number of people should consider this. In like manner, I agree on a huge segment of the centers you have made.spss help
ReplyDeleteThe Supreme court orders for permanent commission to women
ReplyDeleteSupreme court has delivered a judgement, upholding the 2013 verdict of the Delhi High Court, on Feb 17, 2020, asking the government to grant permanent commission to women in the Short Service Commission. SC asked to pass the notification regarding it in the time period of 3 months.
The women cadets are already being absorbed in the various branches of the armed forces, but they are denied the permanent commission. This was a clear violation of the equality and non-discrimination principle enshrined in the constitution of India. The supreme court has destroyed the stereotypes about the physiological features as represented by the government in its submission in the court which deny equal status to women who complete the same criteria as their male counterparts do.
See More Article:https://www.molitics.in/
The baring of your clothes is going to be such you yourself will not return to ground concerning this even once constant call girls in Jaipur city. Such is that the smoothness in her tongue that you simply can beyond question shake on with large rock profound within.
ReplyDeleteGoa Escorts
Jaipur Escorts
Udaipur escorts
Noida escorts
Goa Call Girls
Dial on our error support How to fix QuickBooks Error H505 844-908-0801 to get the solution of all QuickBooks issues and error
ReplyDeleteThanks for sharing an impressive blog post, I always appreciate your quality content.
ReplyDeleteAdult Dating SEO
Body Massage SEO
Cannabis SEO Services
SEO for Bitcoin Websites
Thank you so much for this Post and all the best for your future. You have opened my eyes to varying views on this topic with the interesting. I am satisfied with the arrangement of your post. Thank you..!!!
ReplyDeleteQuickBooks Error H101, H202, H303 or H505
QuickBooks Error H202
Digital marketing is a new trendsetter in the business era, as the best digital marketing agency in USA move drastically in the world of marketing and advertising to promote their brand. Whether you look at USA or globally, there has been a huge shift in marketing, as most of the consumers are aided in their decision-making process with their smartphones, content, influencers, social media, and other customers. In this technology-driven era, top digital marketing company in USA follows digital technologies and channels is an imperative approach to achieve marketing objectives, as well as the right platform to here and address your queries and help you grow.
ReplyDeleteSan Diego Escort Agency San Diego escort firls and San Diego Outcall escorts services with photo at Ladiesofsandiego.com.
ReplyDeleteDesign and order customized tees without essentials. Regardless of whether you need to arrange only one tee, or a hundred, there are no forthright expenses or essentials for your request. Just pick a shirt that you like, add your extraordinary plan to it, and request it for yourself, or even beginning a little online business. Customize Own T-Shirt
ReplyDeleteNice Blog post, Really got much useful information for what I was searching.
ReplyDeletehttp://www.apsense.com/article/what-are-the-services-of-the-clinical-research-consultant.html
https://biotechresearchgroup.com/toxicology-expert-witness/
https://biotechresearchgroup.com/fda-gmp-consultants/
https://biotechresearchgroup.com/know-the-process-through-which-an-otc-drug-undergoes-before-it-is-made-available-in-the-market/
http://www.apsense.com/article/purpose-of-rxtootc-consulting-services.html
https://www.bloglovin.com/@aaryan27/purpose-rx-to-otc-consulting-services-3797219
https://biotechresearchgroup.com/marketing-otc-drugs-legally/
https://medium.com/@aaryan.smith/what-are-the-processes-of-quality-consulting-services-4583a2d0bf67
Hy kbc fans, Check 2019-20 List for your favorite show....
ReplyDeleteYour post always provide information regarding the topic. Thank you for sharing it with us. If you facing any problem regarding Roku Setup than contact our expert to solve your problem.
ReplyDeleteThanks for sharing such an informative post.
ReplyDeleteWe hope you find this article helpful in solving the issues that Troubleshoot PDF and Print Problems with QuickBooks Desktop. Also, if you are facing issues even after performing the solutions provided here, you can call our How to Resolve QuickBooks Error 61686? Team at +1(800)-880-6389 and speak to certified experts.
Your blog always offer some really interesting information. Thank you for sharing it with us. If you facing any problem regarding Roku Device Setup than contact our expert to solve your problem.
ReplyDeletethis is a really useful article for anyone concerned about privacy and cyber security. we will be referencing it on https://www.comparemyvpn.com
ReplyDeleteWe at Animation Dok are a proficient Animation Company in Newark agency providing amazing services to the clients. Whether you are a small enterprise looking for marketing their business or a renowned enterprise re branding the company, we have professionals who can provide the best video to get your video across the audience.
ReplyDeleteBangkok VIP Escort agency is ready to serve your every need, Even we have anal willing escorts in Bangkok.
ReplyDeletehttp://flyfreemedia.com/forums/users/BangkokEscortsAgency
https://www.sparkfun.com/users/1586601
http://smushy-manow.freeescortsite.com/
http://marvelousmay.freeescortsite.com/
http://athletic-aliz.freeescortsite.com/
https://www.edocr.com/v/xybkqm63/WilberRubin/How-to-build-a-strong-relationship-with-Thailand-F
http://www.authorstream.com/Presentation/WilberRubin-4244360-build-strong-relationship-thailand-female-escorts/
http://www.apsense.com/article/how-to-completely-revamp-your-life-with-bangkok-gold-escorts.html
https://topsitenet.com/article/328723-how-to-completely-revamp-your-life-with-bangkok-gold-escorts/
Nice Blog!
ReplyDeleteGet QuickBooks support from our expert to get instant solution regarding any error.
Dial Quickbooks Technical Support Phone Number +1-844-908-0801.
Some experts think that VPN is not good for our business because Google can penalize our business but some people think that we should use VPN for location changing. I will suggest that you should avoid from such kind of activities. Assignment writing services.
ReplyDeletevery helpful!
ReplyDeleteQuickBooks Support provide you live support to fix any error and glitch regarding QuickBooks software.
Dial QuickBooks Support Phone Number +1-844-908-0801.
Nice Blog!
ReplyDeleteWorried about QuickBooks error and glitch Just make a call to get instant solution.
Dial QuickBooks Support Phone Number +1-844-908-0801.
This post is really good and helpful for us. the content of this article is really good.
ReplyDeleteThanks, for sharing the information.Quickbooks file doctor
Purchasing plugin and Setup in WordPress is not easy task if you are looking help and assistance contact 247wpsupport experts. Who is always here to guide you with all the tasks which need to run a successful WordPress blog? Get assistance any time of the day on our WordPress Customer service at & 1 (844) 589 2165 and get instant solution,https://www.bookkippo.com/quickbooks-support/
ReplyDeleteThis is very much great and hope fully nice blog. Every body can easily found her need able information. I am visit first time but I fond many use full article.
ReplyDeleteResolve QuickBooks Unable to Create Accountant’s Copy Issue
Fix QuickBooks error code 1321
Download, Setup, and Update QuickBooks Database Server Manager
How to Fix QuickBooks desktop Error Code 1904
Quickbooks online login Quickbooks Online Login +1-877-715-0222 is one of such applications that have more powerful features and efficient tools for your medium-sized business. It has various advanced features and functionality to QuickBooks Users. With the help of such advanced features, users can create payroll, invoices, sales and balance sheets of the small-sized businesses. It has different propelled features and usefulness to QuickBooks Users. With the assistance of such propelled highlights, clients can make finance, deals and asset reports of the little measured business. It’ll keep a record of every sale, expense, accepting payments, paying your employees and much more Quickbooks Customer Service.
ReplyDeletehttps://www.accountwizy.com/quickbooks-online-login/
Quickbooks online login
Quickbooks Proadvisor
Quickbooks customer service
Quickbooks gmail not working
Quickbooks for mac
Quickbooks Customer Service
Quickbooks Customer Service Number
your blog It was nice thanks for sharing your blog thanks for sharing your blog keep sharing.Quickbooks Online Support
ReplyDeleteNice Blog!
ReplyDeleteQuickBooks error and glitch get instant solution with our 24*7 Live support.
Dial QuickBooks Customer Service +1-844-908-0801.
Nice Blog!
ReplyDeleteFacing error while using QuickBooks get instant solution with our 24*7 live support.
Dial QuickBooks Support Phone Number +1-844-908-0801.
Nice Blog!
ReplyDeletegetting QuickBooks error and glitch get instant solution with our expert.
Dial QuickBooks Customer Support Number +1-844-908-0801.
I generally use easy to install VPNs like Tunnelbear and Cyberghost VPN but I found this article as I was looking to install my own. Thank you for sharing!
ReplyDeleteLos Angeles Escorts
ReplyDeleteNice Blog!
ReplyDeleteFacing error while using QuickBooks get instant solution with our QuickBooks experts.
Dial QuickBooks Support Phone Number Arizona +1-844-908-0801.
very interesting post.this is my first time visit here.i found so mmany interesting stuff in your blog especially its discussion..thanks for the post!
ReplyDeletePrimary School Tutor
Nice Blog!
ReplyDeleteWorried about QuickBooks error and glitch? Get in touch with our QuickBooks expert for instant solution.
Dial QuickBooks Number +1-844-908-0801.
Our Singapore girls are always top class and passionate about spending time with you. An erotic dance can be an excellent way for you to see how flexible and easy going these girls are whenever you need them. At the same time, Singapore escorts can be very romantic and slow. Even that for many men is very sexy and they could cum right away. Dinner dates and other exciting approach is also beautiful. You have to choose wisely from all the call girls. They are all delightful, but still with some differences in their abilities or just preferences. Some prefer gentlemen who know what they want to get out from their companion. Some others are more into younger guys who want to explore women and their unique ability. There won’t be any need to fake something or make everything according to some plan. Everything is possible with your teacher. If you are naughty, this is your real jackpot. Sex toys are just one of the additions that you can have. If you book an incall, you won’t have to worry about what to bring. And you also don’t have to be that super muscular and handsome guy to fit your lady’s taste. They are more about real satisfaction and options that won’t cease the desire for hours. Feel free to read all the rest details from every profile and make your decision.
ReplyDeletesingapore call girl
singapore escort serviceOur Singapore girls are always top class and passionate about spending time with you. An erotic dance can be an excellent way for you to see how flexible and easy going these girls are whenever you need them. At the same time, Singapore escorts can be very romantic and slow. Even that for many men is very sexy and they could cum right away. Dinner dates and other exciting approach is also beautiful. You have to choose wisely from all the call girls. They are all delightful, but still with some differences in their abilities or just preferences. Some prefer gentlemen who know what they want to get out from their companion. Some others are more into younger guys who want to explore women and their unique ability. There won’t be any need to fake something or make everything according to some plan. Everything is possible with your teacher. If you are naughty, this is your real jackpot. Sex toys are just one of the additions that you can have. If you book an incall, you won’t have to worry about what to bring. And you also don’t have to be that super muscular and handsome guy to fit your lady’s taste. They are more about real satisfaction and options that won’t cease the desire for hours. Feel free to read all the rest details from every profile and make your decision.
singapore call girl
singapore escort service
Well explained!
ReplyDeletegetting QuickBooks error and any issues ? get in touch with our QuickBooks expert for efficient solution.
Dial QuickBooks Customer Support Number +1-844-908-0801
QuickBooks Error 3371: QuickBooks could not load the license data. This is one of the most common errors that may occur when you activate or open QuickBooks Desktop. You might see one of these error messages: Could not initialize license properties. You can understand it in a way that Intuit makes it compulsory to have license information stored on your hard drive. By any means, if that information, file, or license data get corrupted, damaged or missing; you can encounter this error code. In case, if the solutions written above do not help you in fixing “QuickBooks Error 3371” or you want any assistance regarding the same. Then, you can contact us our QuickBooks Error Support Number 1-800-865-4183.
ReplyDelete